Ransomware is a type of malware that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. Ransomware attacks have become a major issue in the cybersecurity space. According to Forbes June 2020 research, 51% of organizations have been impacted in the last 12 months alone.
We spoke with Ritesh Agrawal, the CEO and co-founder of Airgap, a Cervin portfolio company in the cybersecurity space, to discuss the issue of ransomware and what companies can do to protect themselves.
Q: Why are ransomware attacks becoming more prevalent?
A: It comes down to one thing — money. Some speculate that it has to do with the rise in cryptocurrency, which is how most ransoms are paid. Since cryptocurrency is so difficult to trace, it has made hackers bolder. Others speculate that challenging economic times, like the ones brought about by COVID-19, have contributed to increased ransomware attacks.
Q: What defenses are companies using against ransomware?
A: Ransomware follows a three-stage attack, and companies can do different things at each stage:
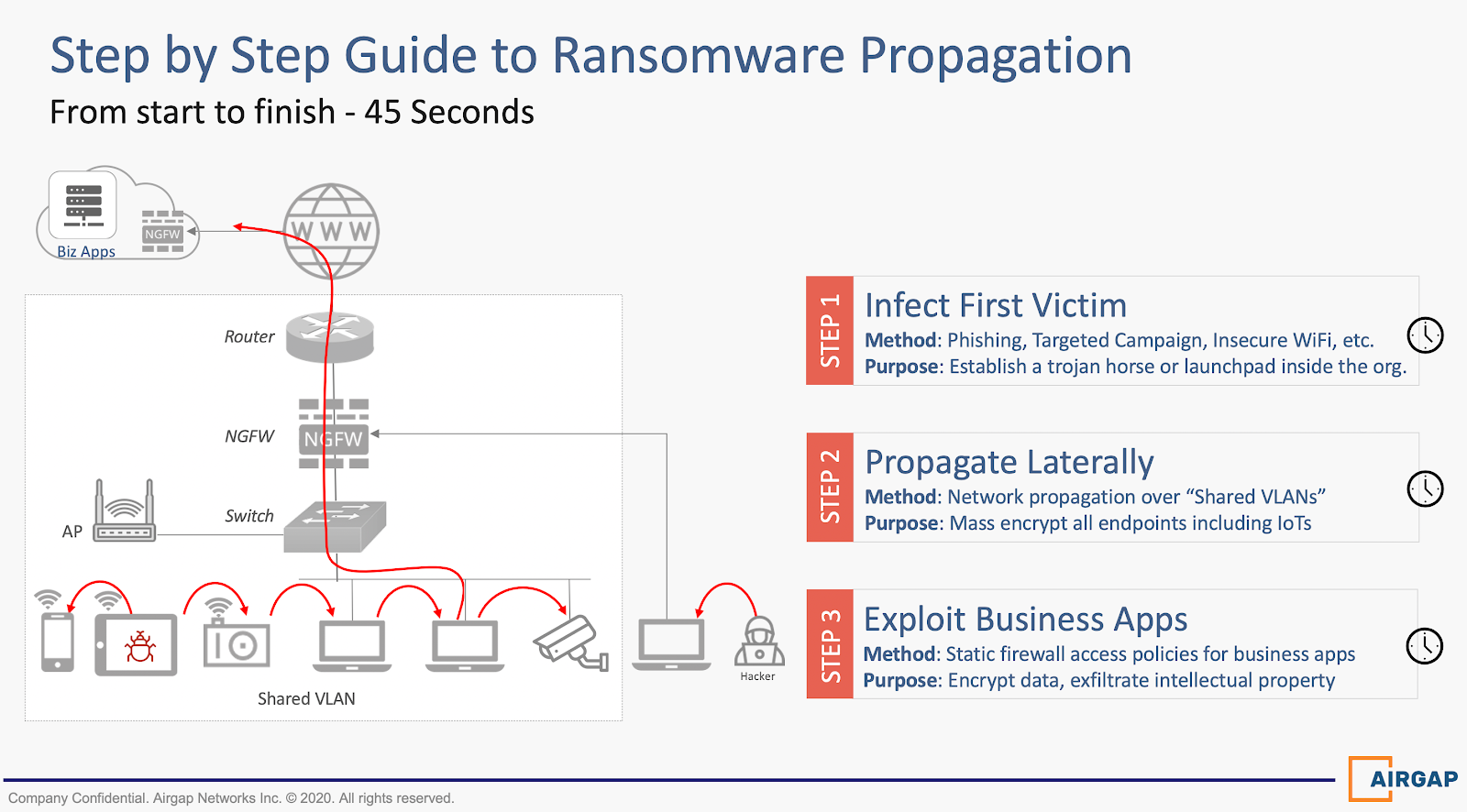
Attack Stage 1
The hackers or bad actors infiltrate the perimeter by exploiting one endpoint. Typically, they target employees and send them a phishing link that downloads malware to their computer if clicked. The purpose is to establish a trojan horse inside the organization.
Current Prevention Techniques
Organizations typically use anti-virus and anti-malware solutions to protect the “first victim”. While these solutions are helpful, they aren’t necessarily sufficient for two reasons:
(1) They won’t work for unmanaged devices such as a smart TV, smart thermostat, smartwatches, or other device connected to an organization’s network.
(2) They take a few minutes to identify a bad actor’s presence, and in that time, ransomware can spread.
Attack Stage 2
Once the organization’s perimeter is breached, the bad actors exploit the flaws in enterprise architecture to propagate the attack by infecting hundreds or thousands of endpoints deployed over a shared network (VLAN).
Current Prevention Techniques
There are no known security solutions that protect against such propagation. Hence organizations often resort to less effective networking or DIY techniques.
Attack Stage 3
Eventually, bad actors leverage authenticated channels from one or more endpoints to infect and encrypt organizations’ crown jewels like file storage, backup systems, ERP systems, etc.
Current Prevention Techniques
Organizations often resort to retrofitting solutions like next-generation firewalls (NGFWs) or web-application firewalls (WAFs) to protect internal applications. Such solutions are only partially effective and still offer network-level access, which results in an increased risk of exposure and exploitation. Alternatively, organizations claim to have robust storage backup plans. However, the bad actors have resorted to stealing the data and threatening the organization to release stolen data into the public domain.
Once the organization is breached, it is important for the SecOps (Security Operations) teams to have a clear remediation plan. However, after talking to hundreds of CIOs, I’ve realized many organizations aren’t well prepared for such an event. When asked, a typical answer I get is “we’d start yanking the cables” — which is not a viable option for any organization.
Q: What are the repercussions on the IT team when a company gets hit by ransomware?
A: The truth is that when attacks happen, someone has to be held accountable, and it’s usually the IT team. They could lose their jobs as a result. This is unfortunate because, in many cases, they didn’t even have the proper tools to deal with the attack in the first place. It’s like sending someone into a battle without proper ammunition and blaming them for losing the battle.
Of course, ransomware attacks have impacts beyond the IT team. An attack can mean damage to the brand, loss of business productivity, and permanent loss of mission-critical business data. The financial impact can be huge and the actual ransom payment can be millions of dollars.

Q: What are some best practices against ransomware attacks as companies transition to remote work?
A: In my opinion, partial remote work will likely become a permanent part of the work environment. No matter where employees work, at the office, at home, at a coffee shop, they need to be protected against ransomware attacks. Given the frequency of attacks, it’s safe to say that the current solutions and best practices are flawed, and alternatives need to be implemented.
Flaw #1: Shared VLANs
Companies routinely deploy thousands of devices over shared virtual local area networks (VLANs). Shared VLANs don’t provide any protection against lateral propagation of the attack. Once any one of the devices connected to the VLAN is infected, all other network devices are vulnerable.
Recommended Solution
Implement a proven Zero Trust model to isolate each device and only allow authorized lateral communication. Any infected device will then be confined, and the attack won’t be able to propagate laterally. Ensure that you pick an agentless Zero Trust solution to protect all devices — managed and unmanaged.
Flaw #2: Network-level access
Consider this, when accessing your bank account online, the bank does not offer access to its IP network. It also provides MFA (multi-factor authentication) to ensure security and protect data. Your business data is just as important; defend it the same way.
Recommended Solution
Implement bank-level security and MFA for your private applications. It just takes a few minutes, no design changes, no agents, and no application changes.
Flaw #3: Ransomware kill switch
Most organizations likely have ransomware infected endpoints, unpatched applications, or insecure legacy protocols operating right now. Some of these systems are available for rent to the highest bidder on the dark web.
Recommended Solution
The best method for the SecOps organization is to have a one-click “ransomware kill switch” that can instantly protect the organization by shutting down access to enterprise crown jewels such as storage systems and all non-critical infrastructure services such as printing or music streaming. Then once everything is safe, turn it back on.
Q: Which of these flaws is Airgap addressing?
A: Airgap is laser-focused on addressing key challenges faced by organizations across the globe. Our platform addresses the fundamental flaws presented by traditional architecture and gaps that aren’t addressed by the traditional security vendors. Our unique and patent-pending Zero Trust Isolation platform prevents ransomware spread by confining it to a single device. We take an identity-centric approach using SSO and MFA for private application access to provide bank-level security. Our one-click “ransomware kill switch” offers immediate action to prevent the spread of ransomware when the organizations are under attack.
Airgap Networks is a Cervin portfolio company, and Ritesh can be reached at ritesh@airgap.io.







